Understanding Cybersecurity Risks in the Logistics Industry

Join Our
Trusted Network
Help protect your business with the load board you can rely on.
Cybercriminals are opportunists. They exploit any vulnerability they can to steal information and make money. All logistics companies are vulnerable, regardless of size, including owner-operators who rely on technology to run their businesses.
As cyber threats in logistics evolve, you need to stay informed and take steps to protect yourself. Learn what owner-operators should know about cybersecurity and practical tips to help you safeguard your business from potential cyberattacks.
Cyberattacks on logistics businesses are becoming more common. To protect yourself, it’s essential to stay informed about cybersecurity risks. Learn what cybersecurity threats owner-operators face and practical steps to secure your business.
Common cyber threats in logistics
Every truck is basically a fully functioning office, with multiple connection points to the internet. Hackers can use these connections to steal data, gain access to trucks, disable vehicles, and snarl your entire operation.
As an owner-operator, knowledge is power. Familiarizing yourself with the common cyber threats is the first important step to keeping your truck or small fleet secure. These are the top threats and scenarios you need to be aware of.
ELD hacking
Electronic logging devices (ELDs) can be vulnerable to hacking attempts. These devices connect to the internet so truck drivers can record and report hours of service. Hackers can exploit vulnerabilities in the ELD’s firmware, software, or communication protocols, either remotely or when they’re close to a truck.
Once someone gains access, they can view sensitive information including driving records, location history, and personal information. By infiltrating a truck’s network, a hacker can manipulate driving records to falsely indicate that a driver has exceeded their permitted hours. This fraudulent information is then used to extort money from either the driver or their employer.
Phishing and smishing
Phishing (via email) and smishing (via SMS) attacks are hacking tactics that trick unwary victims into sharing sensitive information or clicking on malicious links. One of the worst things about this type of attack is that the messages often appear to come from trusted sources.
A message may look like it’s from a broker, a freight company, your bank, or the government, so it’s easy for it to fly under your radar. The message is frequently connected to some type of emergency — it may urge you to take immediate action, like updating your payment information or logging into a website to avoid losing information or money. Scammers are tricky, but you can stay one step ahead of phishing and smishing attempts by being vigilant and educating yourself and everyone you work with about what to look for.
Identity fraud
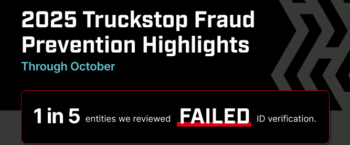
Cybercriminals can hijack professional credentials and impersonate carriers and brokers in the FMCSA Unified Registration System. For example, a cybercriminal can register as a trucking company using a stolen DOT number and operating authority, accept a load from a broker, and then vanish with the cargo.
Identity thieves might also use stolen information to apply for credit cards or loans in your name, which can be a disaster for your business. The good news is that the FMCSA is reworking its registration system in an attempt to crack down on fraud and identity theft.
Office systems
Your truck isn’t the only thing vulnerable to hackers. Just like large carriers, owner-operators who manage small fleets are increasingly integrating their communications, billing, and logistics through single database systems. It’s a connectivity that enhances efficiency, but also makes you a possible target for ransomware, which locks you out of your files with encryption. The hacker then holds your data hostage until you pay the ransom.
A single successful attack on an integrated office system can disrupt an entire company’s supply chain — and there are lots of ways for the bad guys to get inside your virtual house. Hackers can access dispatching software, infiltrate your billing system, and install malware to infect your logistics database.
How to protect yourself from cyber threats in logistics
As an owner-operator, you should be taking steps to reduce your risk of falling victim to cyberattacks. Here are some practical tips to keep you — and your data — safe.
Use uncrackable passwords
A simple but effective anti-hacking tactic is using strong, unique passwords for your email, ELD, online platforms, and other systems. It should go without saying (but we’ll say it anyway), don’t use obvious information like your name, birthdate, or dog’s name.
When creating passwords, use a combination of uppercase and lowercase letters, numbers, and special characters. Password managers can help you generate complex (and secure) passwords and store them safely while making them easy to access. If you’re a Google user, you can run a password health check to find any weak or compromised passwords.
Restrict access to sensitive information
Avoid using public Wi-Fi networks that could allow cybercriminals to break into your internet-connected systems, and configure your smartphone so you get an alert if someone tries to connect to it.
Keep in mind that cybercriminals might use other tactics for intercepting information, like going through dumpsters behind office buildings to find sensitive information. If you have an office, always shred financial documents before disposing of them.
Enable multi-factor authentication
Whenever possible, enable multi-factor authentication (MFA) for your accounts. MFA requires users to provide a second form of verification beyond just a password. This could be a code sent to your email or phone or a secret question you have to answer.
With this extra layer of protection, it’s a lot harder for cybercriminals to access your accounts, even if they manage to obtain your password.
Keep your software and devices up to date
Regularly updating your ELD, smartphone, and computer software is important, because updates often include security patches that address new vulnerabilities.
Hackers constantly search for weaknesses in outdated software to gain unauthorized access to systems and data. Ignoring updates leaves the door open for cybercriminals to access your data and control of your devices.
Look out for bad guys (especially in email and SMS)
Stay vigilant against phishing and smishing attempts and, importantly, make your employees aware of them. Everyone who has access to your systems and data should be trained on what to look for since an unwary employee is often your weakest security link.
Look for unsolicited emails or text messages that ask you to click on links, download attachments, or provide sensitive information. Another giveaway is any business message with misspellings, an odd subject line, or threatening language.
If you receive a suspicious message claiming to be from a company or individual you know, contact them directly. Make sure you use a verified phone number or email address to confirm the legitimacy of any request.
Use a private load board
Consider using a private load board that verifies identities and reduces the risk of fraud. Private load boards, like Truckstop, keep communication in one secure place and validate user identities. This means you can be confident that the person you’re talking to isn’t an imposter, which helps protect you from identity fraud and other scams.
How Truckstop helps protect your business
Truckstop is committed to helping freight professionals grow their businesses while supporting cybersecurity in the logistics industry. By using Truckstop’s private load board, you can connect with verified brokers and shippers, reduce the risk of falling victim to identity fraud and other scams, and find the best rates.
With all your communication and transactions in one secure place, you can grow your business with peace of mind, knowing that Truckstop is working to protect you every step of the way. See how it works by scheduling a demo today.
Get helpful content delivered to your inbox.
Sign up today.
Find high-quality loads fast, get higher rates on every haul, and access tools that make your job easier at every turn.